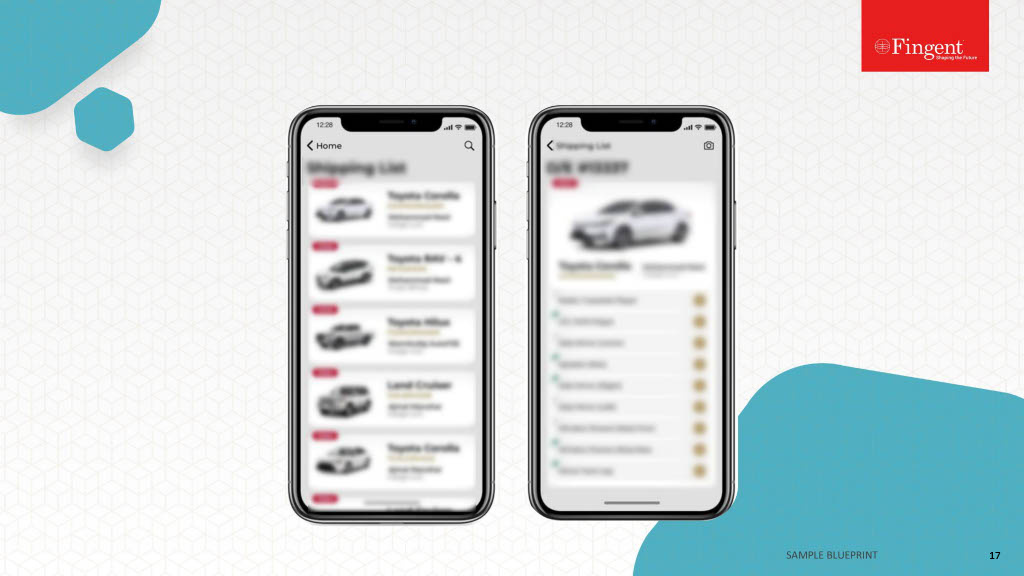
Enterprise Mobility Security Best Practices
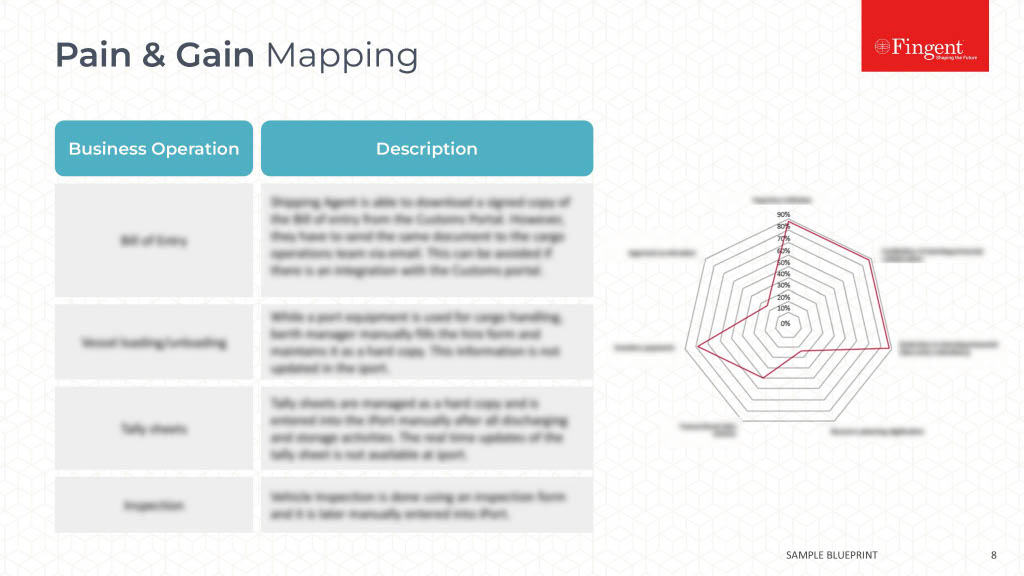
Mobility is the in-thing now. The BYOD wave, coupled with a highly mobile workforce means most employees now access the enterprise network through their mobile devices. However, mobility poses security risks as well. Lurking cyber criminals can easily exploit a vulnerability or security loopholes in a mobile device to gain entry to the network, and wreak havoc. CIOs understand most employees regard mobile devices as the most critical tools for getting work done, but 83% of them are still reluctant to embrace the trend, owing to security concerns.
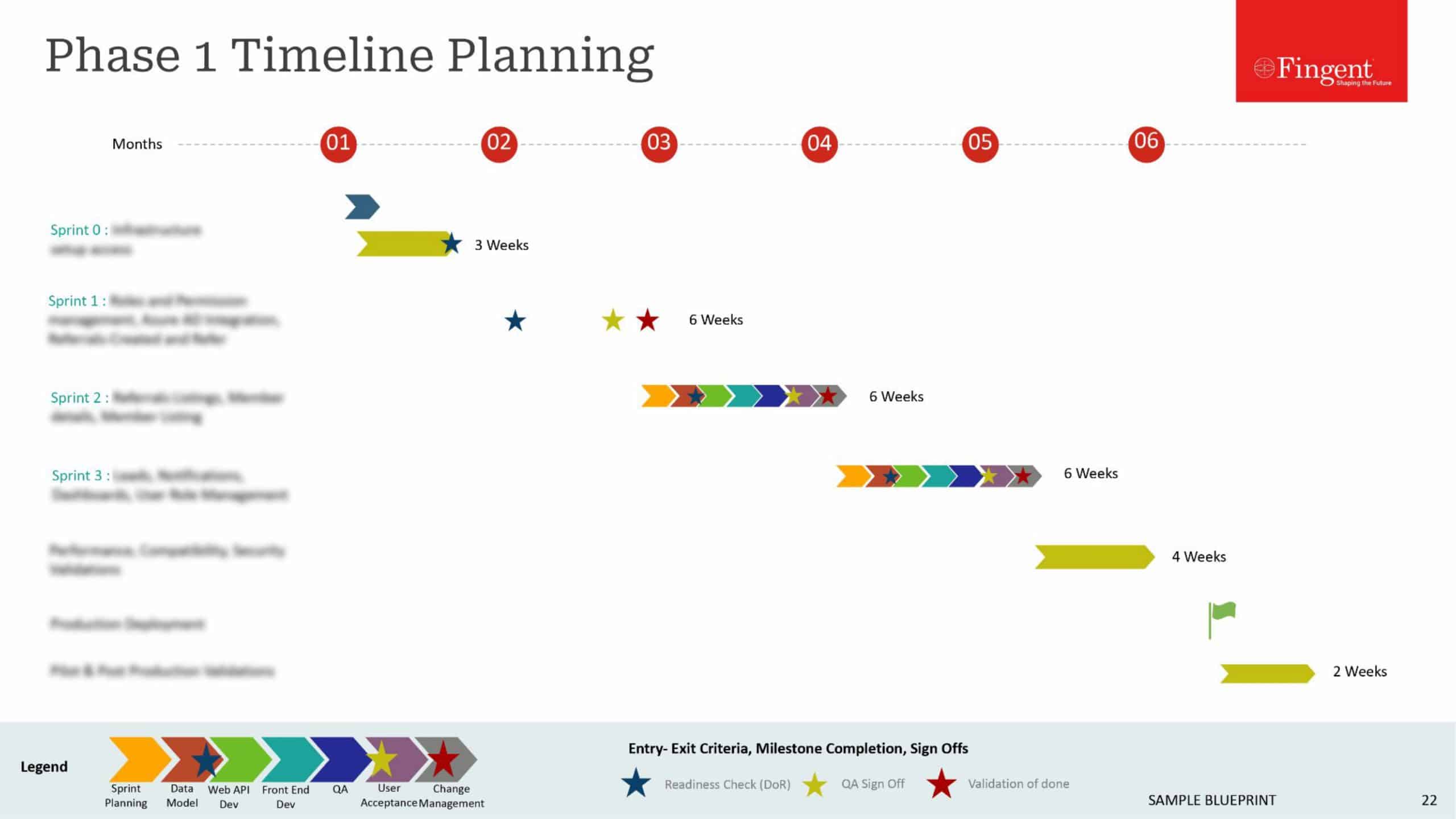
The following are some enterprise mobile security best practices to prevent such security nightmares from coming to pass.
Get the Approach Right
The basic aim of enterprise mobility security is similar to conventional network security, which is to limit exposure to unwanted or uninvited access, and to implement “in depth defense” to harden the system against attacks. Most security systems have multiple layers of protection in place, so that the system remains safe until help arrives, even if one or the first few layers are breached. However, beyond this basic approach, the needs of enterprise mobility security are markedly different.
Securing mobile devices requires a new approach, radically different from protecting conventional endpoints. Mobile devices are moving targets in use outside the organization’s perimeter, and as such traditional security layers such as the firewalls, spam and content filtering, and many other tools are ineffective.
Mobile operating systems such as Android and iOS are especially susceptible to malware attacks, in the same way Windows and Linux are vulnerable. Anti-malware software, updated on a regular basis, is the basic security tool for mobile devices. Any sound enterprise mobility security policy would recommend a sound anti-malware suite, with policies for keeping it updated.
Likewise, encryption is the name of the game for keeping corporate data and intellectual property safe in the Wild West that is cyberspace. Wireless communication is easy to intercept and snoop, making a strong case for encrypting all sensitive communication going in and out of mobile devices. There is also a good case for using VPNs that include encryption and strong authentication capabilities, to access cloud based systems or other remote services from mobile devices.
Remote wipe and lock, and ability to track the location of the mobile devices are also basic security features for enterprise mobility.
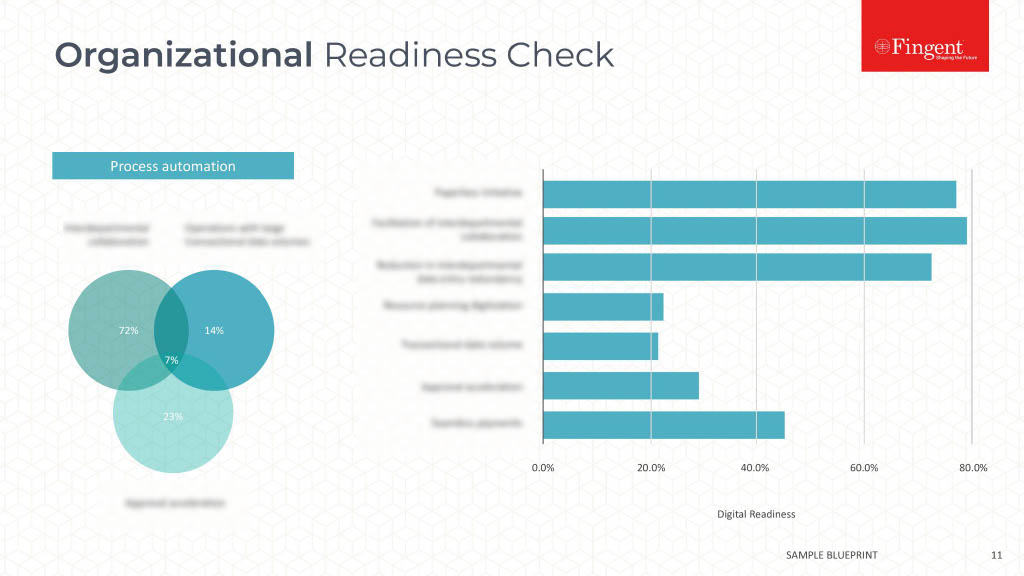
Have Strong Authentication in Place
Mobile devices are especially vulnerable to theft. Eight out of ten CIO’s believe smartphones increase organizational vulnerability through interception of data in transit or through device theft.
Any enterprise security best practice requires strong authentication mechanisms that go beyond conventional passwords.
Built-in biometrics, leveraging the smartphone’s facial recognition capabilities, fingerprint scanners, and voiceprint recognition offer a high level of security. Opt for multi-layered authentication, with add-on device passwords, so that the system does not give automatic access to sensitive information through any endpoint device.
Hypersensitive companies could program to wipe off data from the smartphone automatically, on encountering repeated failed login attempts.
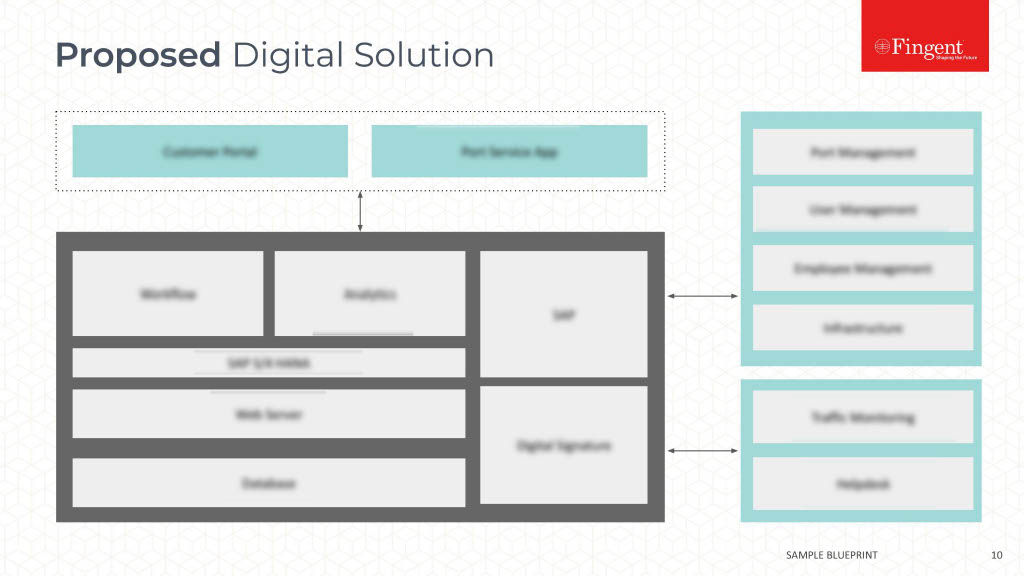
Control Third-party Software
Third party software, which may come with latent vulnerabilities, such as black gateways, built-in back doors and drive-by download of rogue software, are loose ends in enterprise mobile security. In a perfect world, the enterprise could eliminate third-party software in favor on in-house enterprise mobility apps, but such an approach is a non-starter for most enterprises, owing to practical considerations and limitation of resources to develop custom apps. The next best thing for enterprises is to lay down policies that regulate the use of third-party apps. The policy could also white-list safe apps, or black-list apps dangerous for the network.
Many enterprises are now toying with developing their internal app stores that vets apps suitable for download by enterprise users.
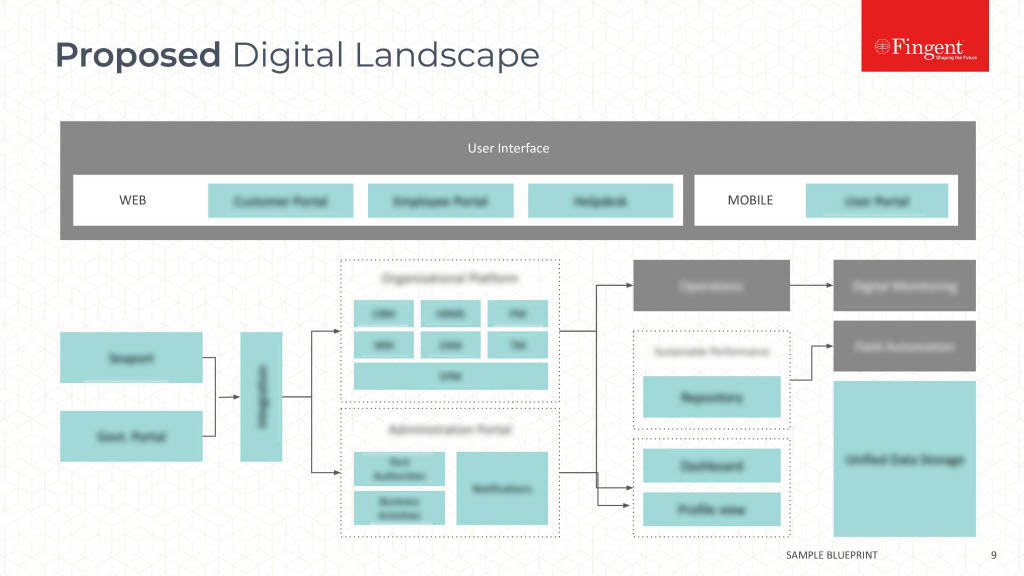
Have Effective Control over the Network
There is no shortcut to having an effective control over the network. In the BYOD era, it is essential to have an up-to-date inventory of all devices authorized to access the network, and nip access of unauthorized devices in the bud.
Creating secured mobile gateways also enhances security in a big way. Securing the network is a team effort. The IT manager and the business manager needs to work together to list down the use-cases, systems and applications mobile users really need to access. Mobile traffic could then be directed through special gateways, complete with customized firewalls, content filtering, and other security controls enabled.
Another best practice is to make BYOD users log on to a remote virtual work environment, through VPN. In such sessions, only the screen output from work applications and systems transmits to the mobile device, and the data does not persist once the remote session ends.
It is also a good idea to conduct penetration testing on the network on a periodic basis, to identify and fix any loose ends.
Have Effective Control over the Device
The configuration of mobile devices is just as important as the choice of mobile devices. Best security practices dictate hiding Bluetooth from discovery, or disabling it altogether, and configuring the device to avoid unsecured wireless networks. A management client application, downloaded on the BYOD device, enable users to comply with such regulations.
Mobile hyper-visors and containers, especially useful for BYOD devices, enable enterprise system administrators to manage apps, data, policies and settings within a container on the employee’s personal device without such interventions intruding into personal content.
While there is a strong case for security, going overboard with security can impede usability. The trick is to strike a fine balance between effective security that is non-disruptive, and UX. It requires considerable experience and expertise to strike such a fine balance, and we have such expertise. Get in touch with us today, to leverage our talented team, who have several years of experience in securing even the most complex and diverse of all enterprise mobility networks.
Stay up to date on what's new

Recommended Posts

27 Nov 2019
AI and Facial Recognition: Innovative Advances & Future Impact
Facial Recognition Technology - What’s In Store For The Future When Facebook started automatically tagging faces in uploaded images, nobody realized that this facial recognition technology would hike up to……
Featured Blogs
Stay up to date on
what's new
















 US
US Insurance
Insurance