Making Sense of the Recent Ransomware Attacks: Wannacry Malware
Wannacry? If you have been inflicted with this latest piece of deadly malware that is wreaking havoc in cyberspace, there’s little else to do but cry! However, understanding what the menace is, and taking basic precautions would save you the tears, allowing you to remain safe and be spared of the data carnage presently underway.
What is Wannacry malware?
Wannacry is a ransomware malware and worm, which has affected computer systems running on Microsoft Windows operating system, at a global scale. The malware, the deadliest one in 2017 so far, started to spread last week, taking over files stored in the infected systems, and demanding $300 in bitcoins, to restore access. Users were also warned the amount would double after three days, and the ‘captured’ files would be deleted irrecoverably if the ransom is not paid within seven days.
It spreads laterally between computers on the same LAN by using a vulnerability in implementations of Server Message Block (SMB) in Windows Systems. The exploit is called ETERNALBLUE. The worst affected are financial institutions, academic institutions, and other businesses attack. It is possible the perpetrators specifically targeted organizations and individuals with sensitive data they cannot afford to lose.
Ransomware is a type of malware that gets into a system by stealth, exploiting some latent vulnerability. Once it enters and installs itself in the system, it encrypts files on the hard drive, and demand payment for the encryption key.
Where is it spreading?
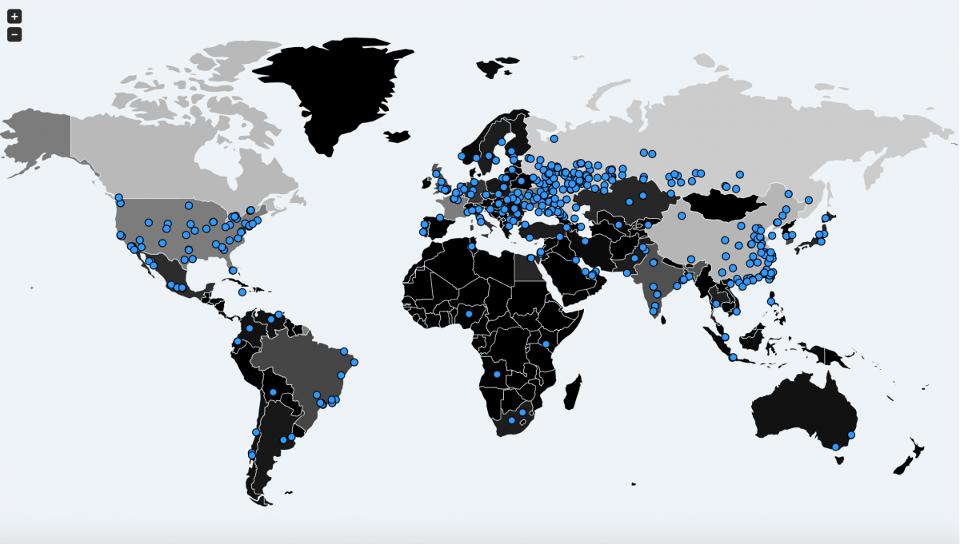
Wannacry has taken the world by storm, affecting thousands of computers in over 150 countries. At last count, it has impacted over 10,000 organizations and over 200,000 individuals, spread across 150 countries. The ransomware mutates itself, spreading from one system to another in different ways.
Among the most high-profile victims have been FedEx, the US-based delivery company, Renault factories in France, the National Health Service in the UK, several telecom and gas companies in Spain, and thousands of other users, from corporate to small businesses, and from non-profits to individuals. While the most high-profile attacks have been in Europe, China and India are especially hard-hit, considering the sheer number of victims, and a large number of systems running on Windows XP and other legacy variants of the OS.
Who are the Perpetrators?
As of now, the perpetrators of the attack are not known. The ransom is to be paid in bitcoins, which are hard to trace. Microsoft, in the line of fire, as Windows systems are the ones coming under attack, gave an indication of the tool used in these attacks being developed by the US National Security Agency (NSA), and now stolen by hackers. It is customary for the NSA to keep a war-chest of cyber-weapons ready, a controversial practice by any account, and the danger of which has now become apparent.
Snowden shines a light on the Shadow Brokers
“If NSA had privately disclosed the flaw used to attack hospitals when they *found* it, not when they lost it, this may not have happened,” NSA whistleblower Edward Snowden says.
Nevertheless, with investigators across the world working on the case, it is only a matter of time before the perpetrators are unearthed, and hopefully, brought to book. Some of the usual suspects, such as Russia, have categorically denied their involvement.
Is the threat over?
One would have thought the malware would have subsided by now after a wave drowned thousands of unsuspecting users in the first few hours of the attack. While there are reports of the attack slowing down, the threat is far from over. There were reports of fresh attacks in Asia and Europe on Monday. At an individual level, several inboxes still have “landmines” in them, mail with attachments that if opened could trigger the attack in the system. There are also reports of a new and deadlier variant of the attack that infects users directly through a malicious link on hacked websites, without requiring users to download an attachment.
There is light at the end of the tunnel though. A UK security researcher discovered a “kill switch” in the rogue software’s code, albeit accidentally. The discovery does not undo the damage already done, but stops the malware in its tracks, preventing its spread to new computers. Also, the possibility of several “copy cat” variants of the attack that will not have the same “kill switch” is also a real possibility.
Precautions to Take
Trying to take remedial measures after being greeting with the red screen of “WannaCry” is like bolting the door after the horse has bolted. The best cure is prevention. Computer users would do be on their alert, and especially consider the following precautions.
- Maintain backups of all critical data and important files in a Google drive, or in an offline hard disk, CD, pen drive, or any other source. The ransomware encrypts the file on the hard drive of the system, rendering it inaccessible to the user. With a backup in hand, users can retrieve the data easily and need not even consider paying the demanded ransom.
- Do not open any mail from unknown senders, and especially avoid spam mail like plague. This is a best practice for all times, and more so in the present troubled times, where any unsolicited mail, even from known accounts, need to be looked upon with suspicion and extreme caution. The safest approach is not to open any attachment or click on any URL in the email, without confirming the sender actually send it. Wannacry is reportedly slipping in malware through common file extensions such as pdf, ppt, doc and tiff, along with media files such as MP4 and MKV files, meaning every file is a potential landmine. Executable files, ending with .exe or .js are especially dangerous. Likewise, be especially wary of shortened URLs. The safest approach is not to download any files or click on any link unless absolutely required.
- The internet is the lifeblood of the ransomware and any cyber attack for that matter. If a system gets affected, the ransomware tries to spread itself rapidly by searching for other unpatched, vulnerable Microsoft PCs in the same local network. It also looks out for any random host on a wider internet. Manually disconnecting the system from the internet at the slightest hint of infection or suspicious behavior may just save the day. Seek professional held when restarting the system.
“Wcrypt mainly penetrates through the SMB ports, so if you block the ports 135 and 445 through which the virus penetrates (in most cases they are not used by ordinary users) you can prevent its spread.“- Akhil S, Ethical Hacker, Fingent Technologies
- Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Access only legitimate and trusted websites. Stay well clear of dubious and unknown sites, especially torrents.
- Shun pirated software, which would invariably have a host of vulnerabilities, and no support or patch updates to effect a fix.
- Update the systems. The main reason why the virus could spread the way it did was because many users fail to keep their systems up-to-date. This kind of attacks thrives on vulnerabilities that exist in the operating system and source code of software that has not been updated. Make sure all software are updated with the latest patch release, and preferably with the latest version as well. Microsoft released an update, Microsoft Security Bulletin MS17-010 as early as March, to tackle the specific the problem involved in the latest attack, but many users have still not downloaded it.
- If there is any incident that illustrates the need for a good antivirus or antimalware suite, this is it. Install and update a good antimalware suite, if not already in place.
As of now, the malware is limited to Windows systems, making other OS such as Android and Ubuntu a safe bet. However, there is nothing preventing a new variant to inflict other operating systems as well, making it expedient for all users to be on high alert.
What to do in case of becoming a victim?
At this point of time, there is precious little to do if an attack has already locked down the files in the computer. The only practical option is to reformat the system and start afresh. Contact the law enforcement and report the attack, though.
The UK’s National Crime Agency, and also most cyber-security experts advise users infected by the malware not to pay the required ransom. Even without any ethical considerations at play, there is no guarantee the systems will be restored even if payment is made. Worse, payment may just embolden the gang behind the operation to demand more.
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



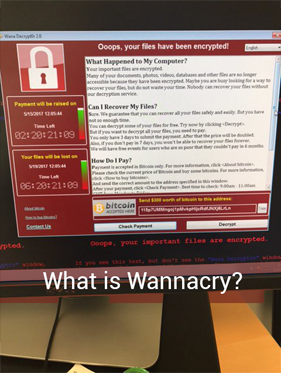
 So far, Criminals behind WannaCry Ransomware have received nearly 100 payments from victims, in 28.56Bitcoins = $49,603.
So far, Criminals behind WannaCry Ransomware have received nearly 100 payments from victims, in 28.56Bitcoins = $49,603.










